Chapter 2: Proactive Detection and Mitigation
Proactive threat mitigation involves identifying and addressing potential risks and vulnerabilities before they can be exploited by malicious actors. It’s a proactive approach to security that aims to minimize the impact of security incidents or breaches by taking preventive measures. Here are some key aspects:
- Risk Assessment: This involves identifying potential threats and vulnerabilities to your systems, networks, or data. It often includes analyzing past security incidents, assessing the current security posture, and evaluating the potential impact of various threats.
- Security Controls Implementation: Implementing security controls such as firewalls, intrusion detection systems, encryption, access controls, and security patches can help mitigate known vulnerabilities and prevent unauthorized access to systems and data.
- Continuous Monitoring: Monitoring systems and networks for suspicious activities or anomalies can help detect potential security threats early. This includes monitoring network traffic, system logs, and user behavior for any signs of unusual activity.
- Threat Intelligence: Utilizing threat intelligence sources to stay informed about emerging threats, attack techniques, and vulnerabilities can help organizations proactively identify and mitigate potential security risks.
- Incident Response Planning: Developing and regularly testing an incident response plan can help organizations effectively respond to security incidents when they occur, minimizing the impact on operations and reducing recovery time.
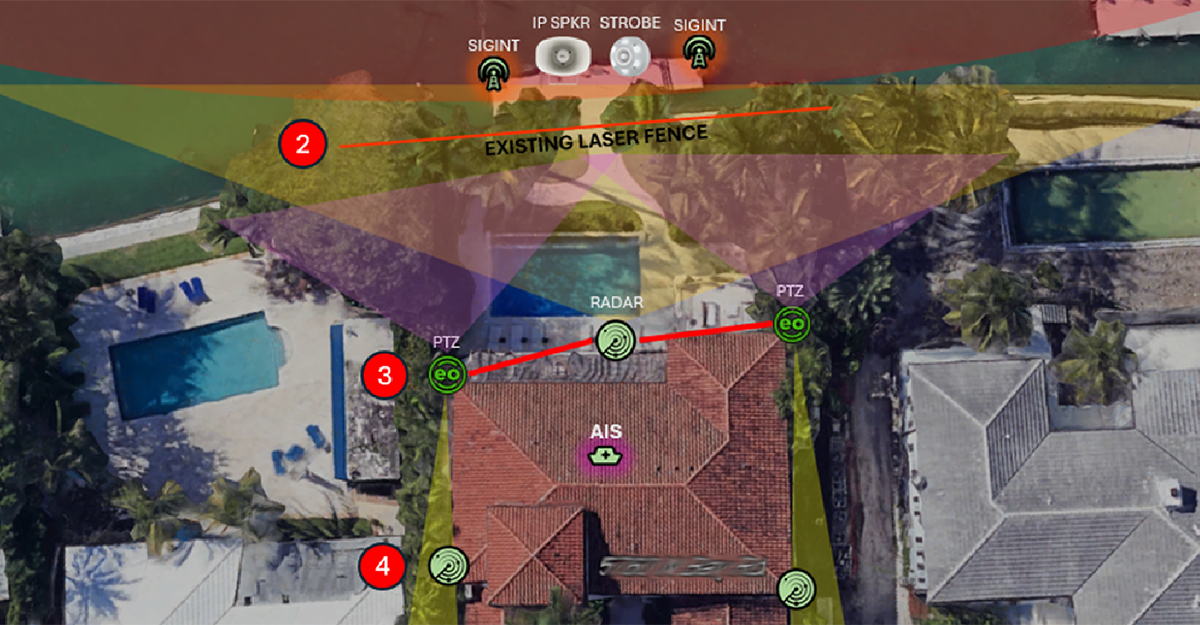
Overall, proactive threat mitigation requires a combination of technical controls, security awareness training, and ongoing monitoring and assessment to effectively mitigate security risks and protect against potential threats. Blueforce and our partners weave it all together and creates threat “learning” that is used to alert all concerned when anomalies are detected. To learn more, check out our new eBook, 5 PHYSICAL SECURITY CONSIDERATIONS FOR RESIDENTIAL AND ENTERPRISE PROTECTION.
DOWNLOAD EBOOK


