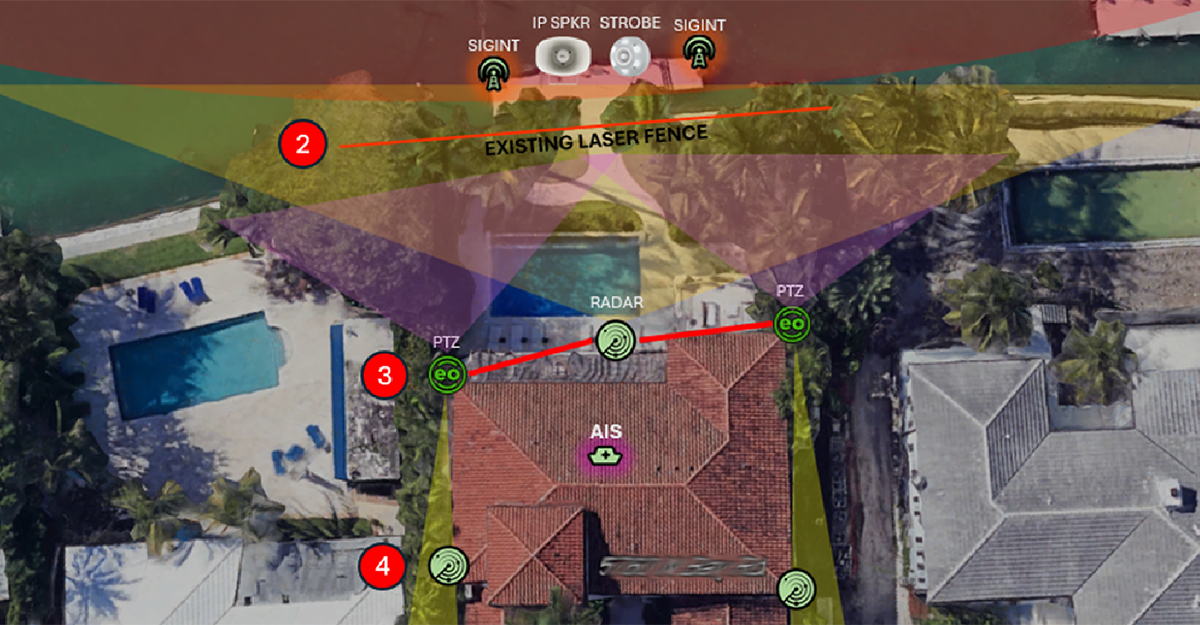
Mission Ready: Public Safety at the Speed of Relevance
Today’s public safety agencies face evolving threats across both the natural and manmade spectrum—requiring instant coordination, verified data, and trustable insights from the scene to the command post. Blueforce and SourceFly’s integrated Edge Intelligence solutions empower responders and emergency managers to execute with real-time clarity, adaptive control, and AI-augmented foresight. Strategy to Execution: Chief to First Responder From municipal emergency managers to incident commanders in the field,...
Read More