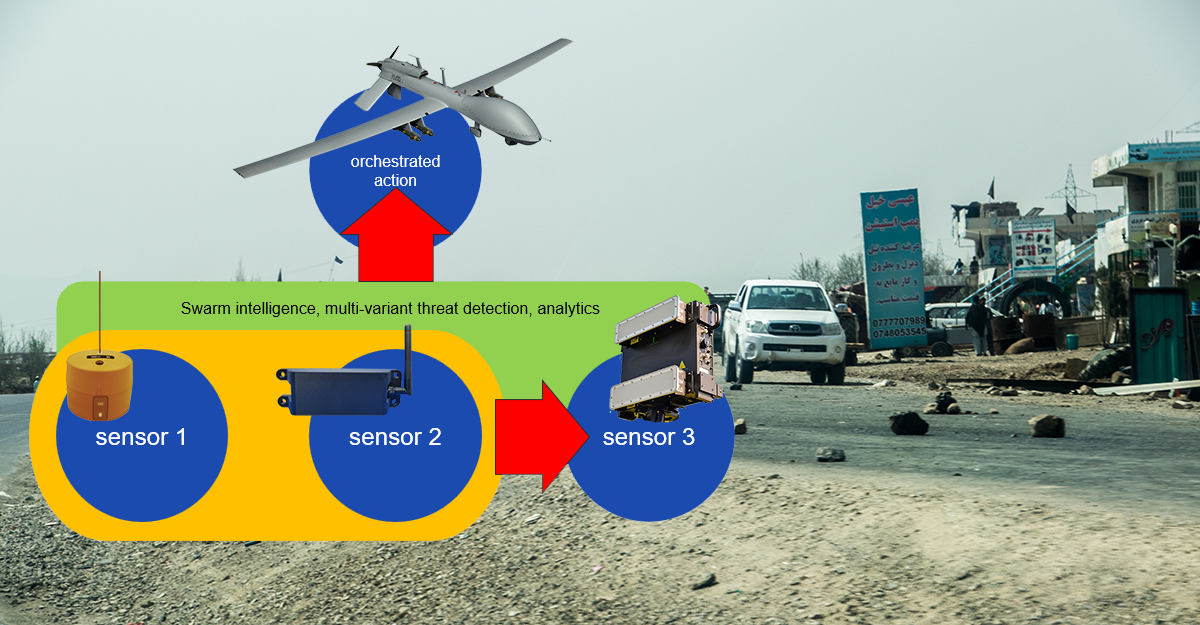
Geopolitical and even transnational shaping of highly mobile and violent burglary rings has prompted discussion and transactions across our business. These now include repeatable "method of operations" (MO's), but also alarming tactics per compound breaches, but also armed incursions and methods that include targeted communities and homes (largely, intelligence-based identification of targets of opportunities). This is not our parent's worry of threat to our families. Specifically,...
Read MoreThe 2022 Blueforce Texas Road Show
The 2022 Blueforce Texas Road Show gives you hands-on access to the latest in Public Safety, Safe Campus, and Autonomous Platform technologies. The Road Show kicks off Tuesday October 11, 2022 in Houston. For more information, click here…