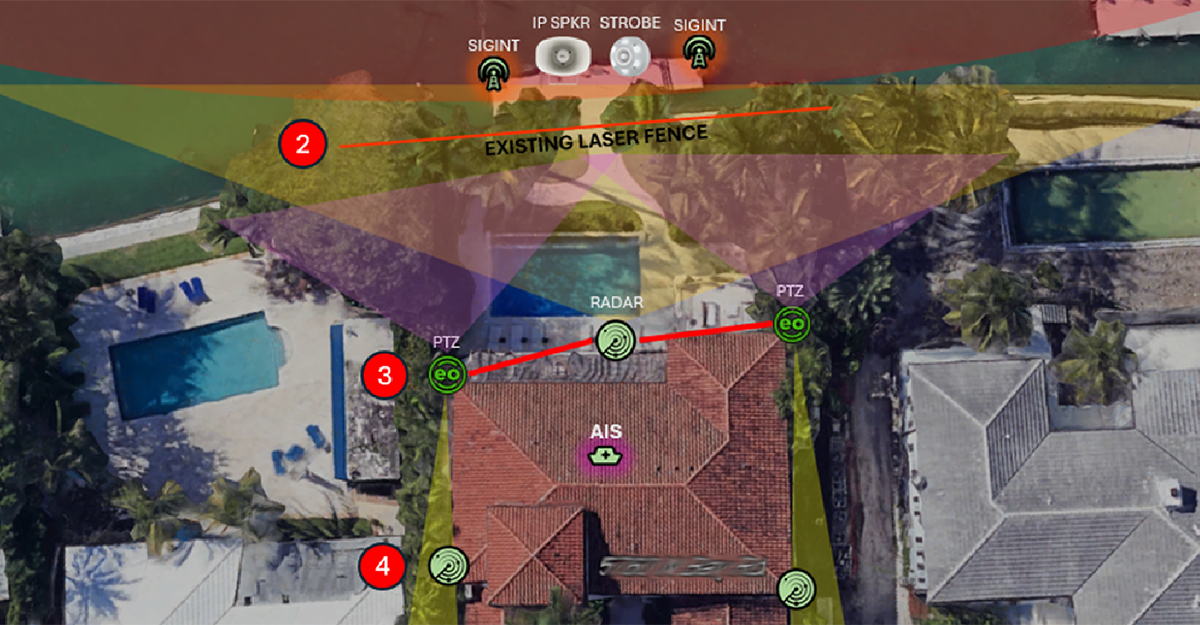
National Security and ISR Superiority: Decision Dominance at Machine Speed
Mission Ready: Decision Dominance at Machine Speed Adversaries are evolving rapidly. While we watched in pain on 9/11, mass casualty tactics were unfolding in real time. Now, we watch as Ukraine stands up to Russia using non-conventional delivery platforms with total orchestration, and winning (but with horrific attrition). Winning today’s hybrid conflicts requires ground truth intelligence that adapts, coordinates, and acts across air, land, sea, cyber,...
Read More