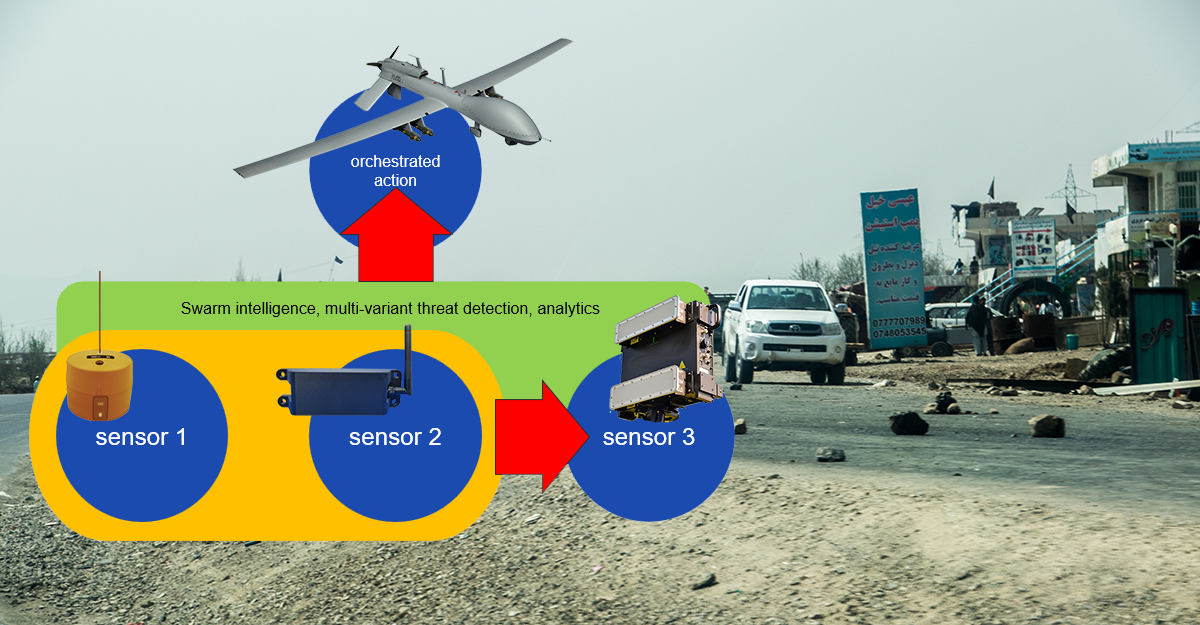
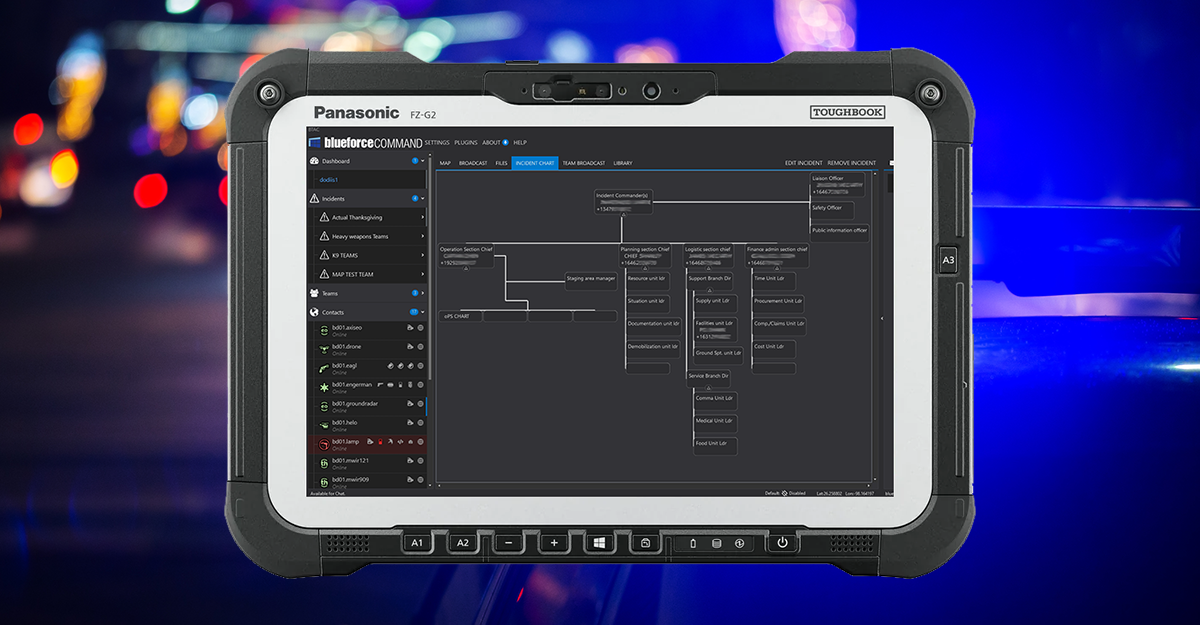
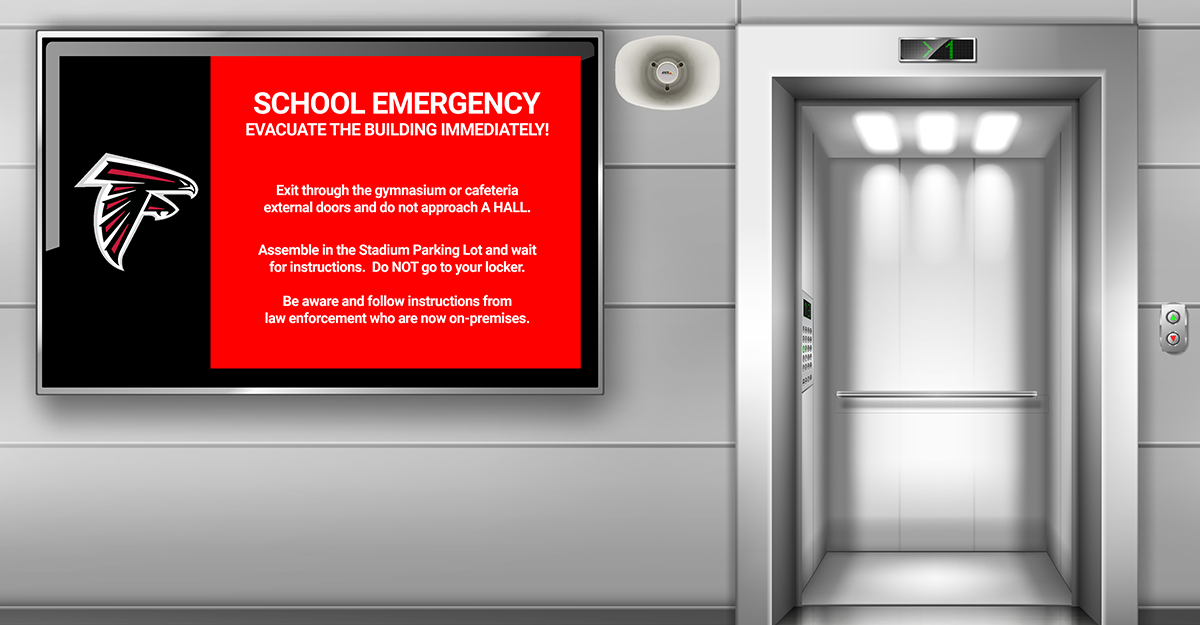
By Morgan Greene, GM National Security Markets, Blueforce Development Corporation We are often asked: What does Blueforce do in the Federal, National Defense, and Intelligence Community spaces? Are you guys the that blueforce tracker stuff? Dots on maps like TAK, right?!? Does it do this JADC2 stuff I’ve been hearing about? No, we have no relation or connection to your experience with blueforce tracker, although we...
Read MoreThe 2022 Blueforce Texas Road Show
The 2022 Blueforce Texas Road Show gives you hands-on access to the latest in Public Safety, Safe Campus, and Autonomous Platform technologies. The Road Show kicks off Tuesday October 11, 2022 in Houston. For more information, click here…