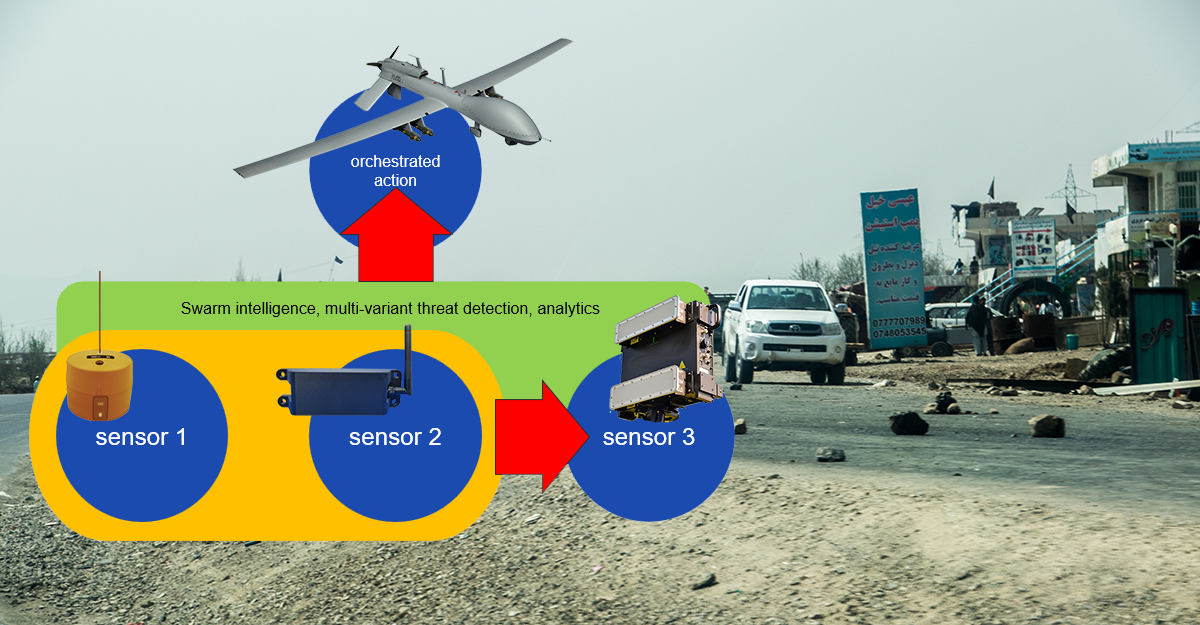
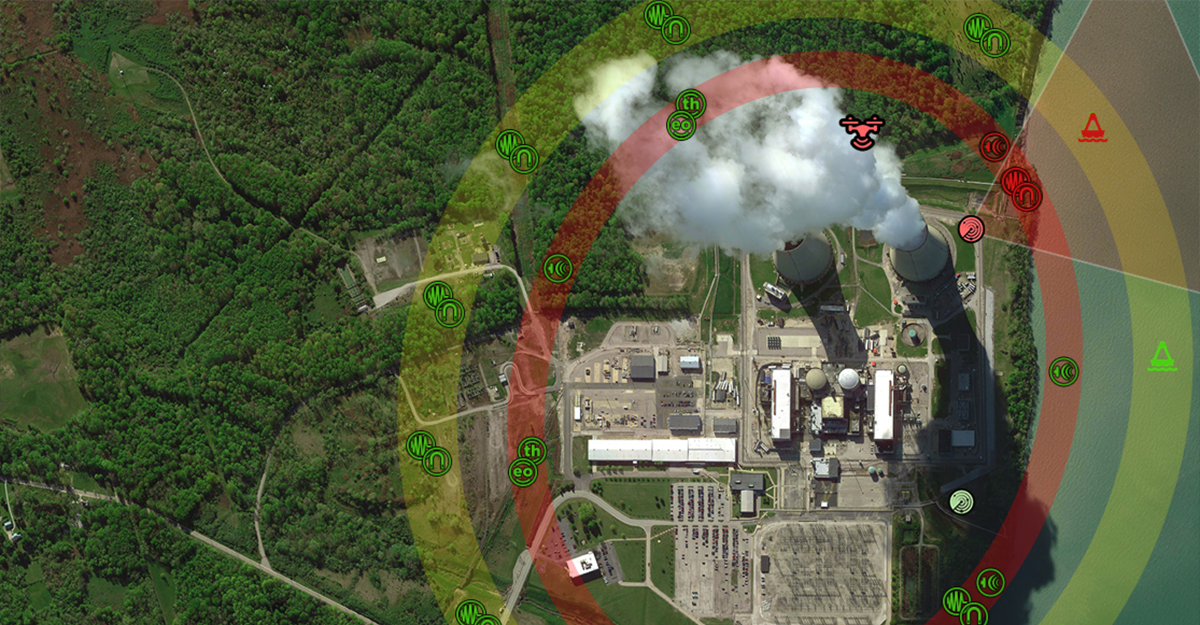
Drone incursions on stadiums, events, and even private property present a range of security issues, primarily due to their potential for unauthorized surveillance, disruption, and even use as an inexpensive means to launch an offensive attack. One significant concern is the risk of drones being used for reconnaissance purposes, allowing individuals with malicious intent to gather intelligence on security vulnerabilities, crowd movements, signal intelligence, and even...
Read MoreThe 2022 Blueforce Texas Road Show
The 2022 Blueforce Texas Road Show gives you hands-on access to the latest in Public Safety, Safe Campus, and Autonomous Platform technologies. The Road Show kicks off Tuesday October 11, 2022 in Houston. For more information, click here…