Blueforce Development Corporation and SourceFly Announce Strategic Partnership to Advance AI Enabled Edge-to-Hybrid Cloud Solutions
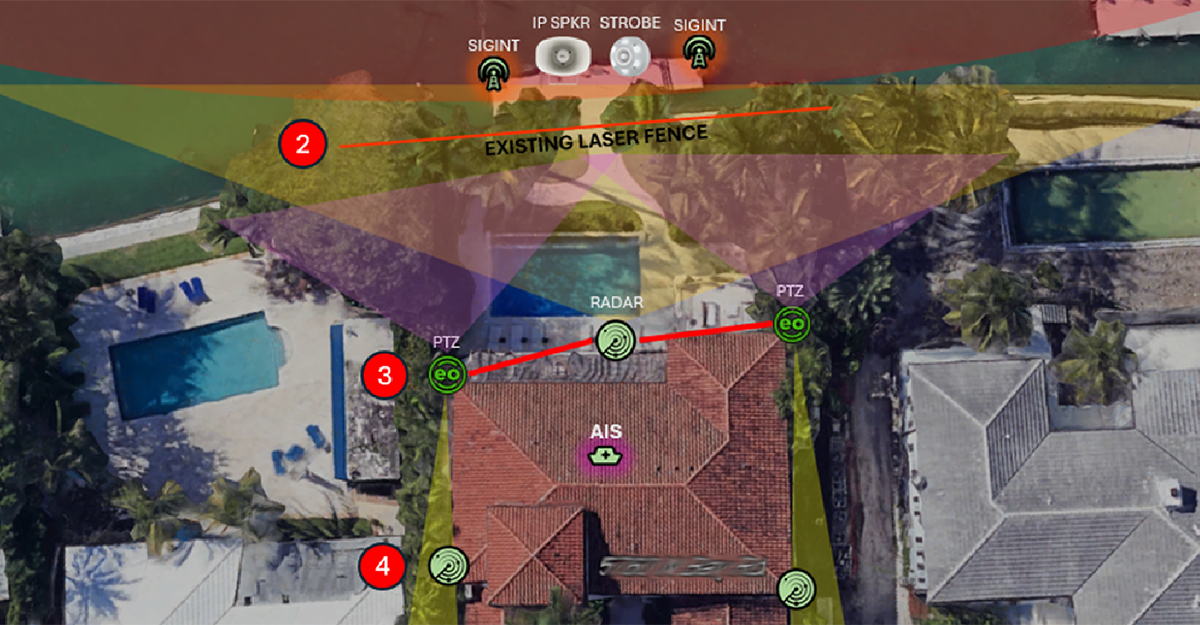
NEWBURYPORT, MA– June 12, 2025 – Blueforce Development Corporation, a leader in AI enabled edge IoT and Command and Control software, and SourceFly, a cloud computing and data analytics services provider, have formed a strategic partnership aimed at accelerating edge-to-hybrid cloud solutions. This alliance will focus on enhancing interoperability and scalability for government agencies and industry clients. Partnership Overview This collaboration combines expertise and capabilities of Blueforce's...
Read More