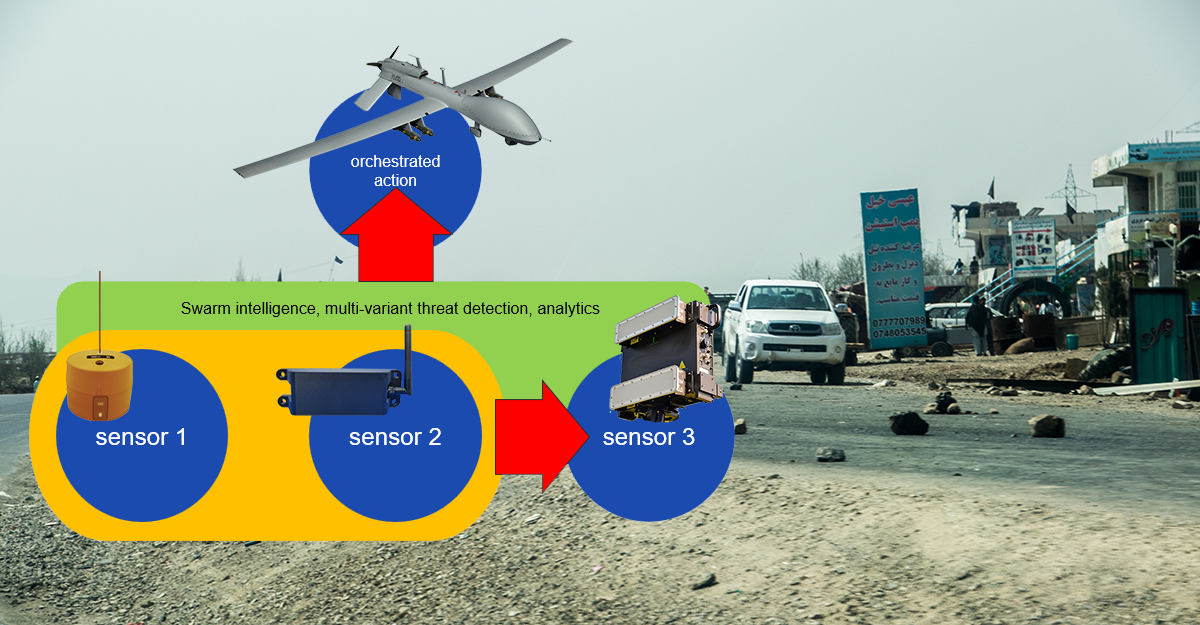
By Andrew Winkler, Thunderbolt Solutions The use of UxVs (aka Drones) is growing exponentially. Their value is undeniable. For many applications, a formation or group of drones is warranted and can provide unparalleled value and moves towards valueSQUARED. Today's market is platform centric. More capability means more payload which drives the hard choice between bigger platform or less endurance. Bigger platforms mean more complex operations and regulatory...
Read MoreThe 2022 Blueforce Texas Road Show
The 2022 Blueforce Texas Road Show gives you hands-on access to the latest in Public Safety, Safe Campus, and Autonomous Platform technologies. The Road Show kicks off Tuesday October 11, 2022 in Houston. For more information, click here…