Innovative Mobile Sensors and Solutions for Worldwide Public Safety and Commercial Aviation
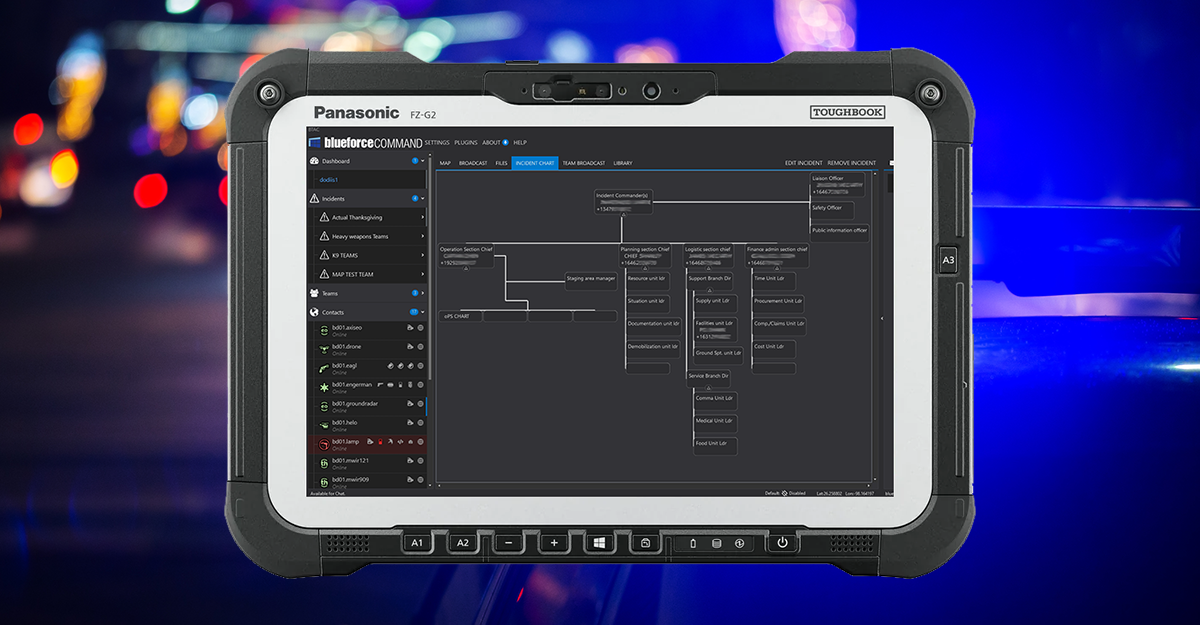
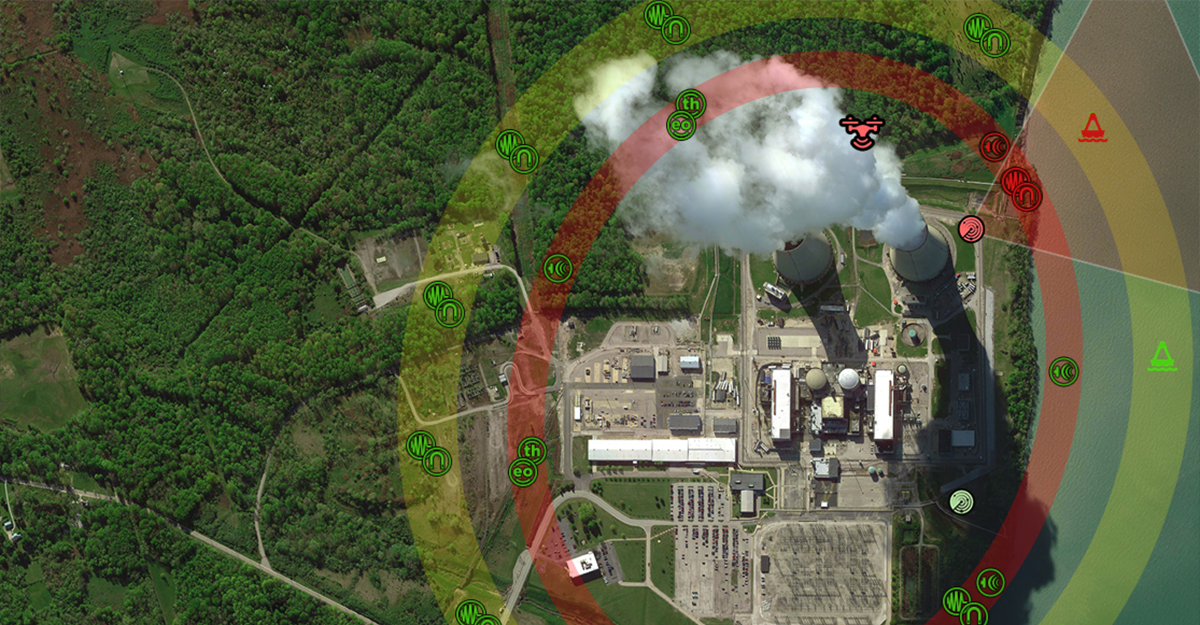
WASHINGTON, March 22, 2023 – Airbus U.S. Space & Defense, Inc., has announced new partnerships to provide powerful mission critical communications and productivity solutions for the national security, public safety and enterprise markets. Airbus is partnering with Blueforce Development Corp., Common Objects, Catalyst Communications Technologies, Inc., and Exacom to provide a complete and best-in-class solution for customers using the Airbus Agnet MCx (Mission Critical Push to...
Read More